Identify and Eliminate Your Cybersecurity Vulnerabilities
Protect your business
from potential threats
with our expert cybersecurity
vulnerability assessment service.
Don’t wait, it’s all out there about you already.
Cybersecurity breaches
can cause irreparable damage
to your business.
Don’t wait until it’s too late
to protect yourself.
Our expert team
of cybersecurity exposure professionals
can help you
identify vulnerabilities in your systems
and eliminate potential threats.
Expert Assessment, Personalized Exposure Report
Our team of cybersecurity experts
will conduct a thorough assessment of your exposed systems
and provide you with a personalized report
that highlights vulnerabilities
and provides actionable solutions to eliminate them.
We’ll work with you every step of the way
to ensure that your business is fully protected.
All we need is your domain name and your consent.
We look at what is exposed.
Trusted By Businesses Like Yours
Our critical infrastructure and government clients
trust us to provide them with
the highest quality cybersecurity services.
With years of experience and a proven track record,
we’re the trusted choice for data-sensitive businesses of all sizes.
This is how it works
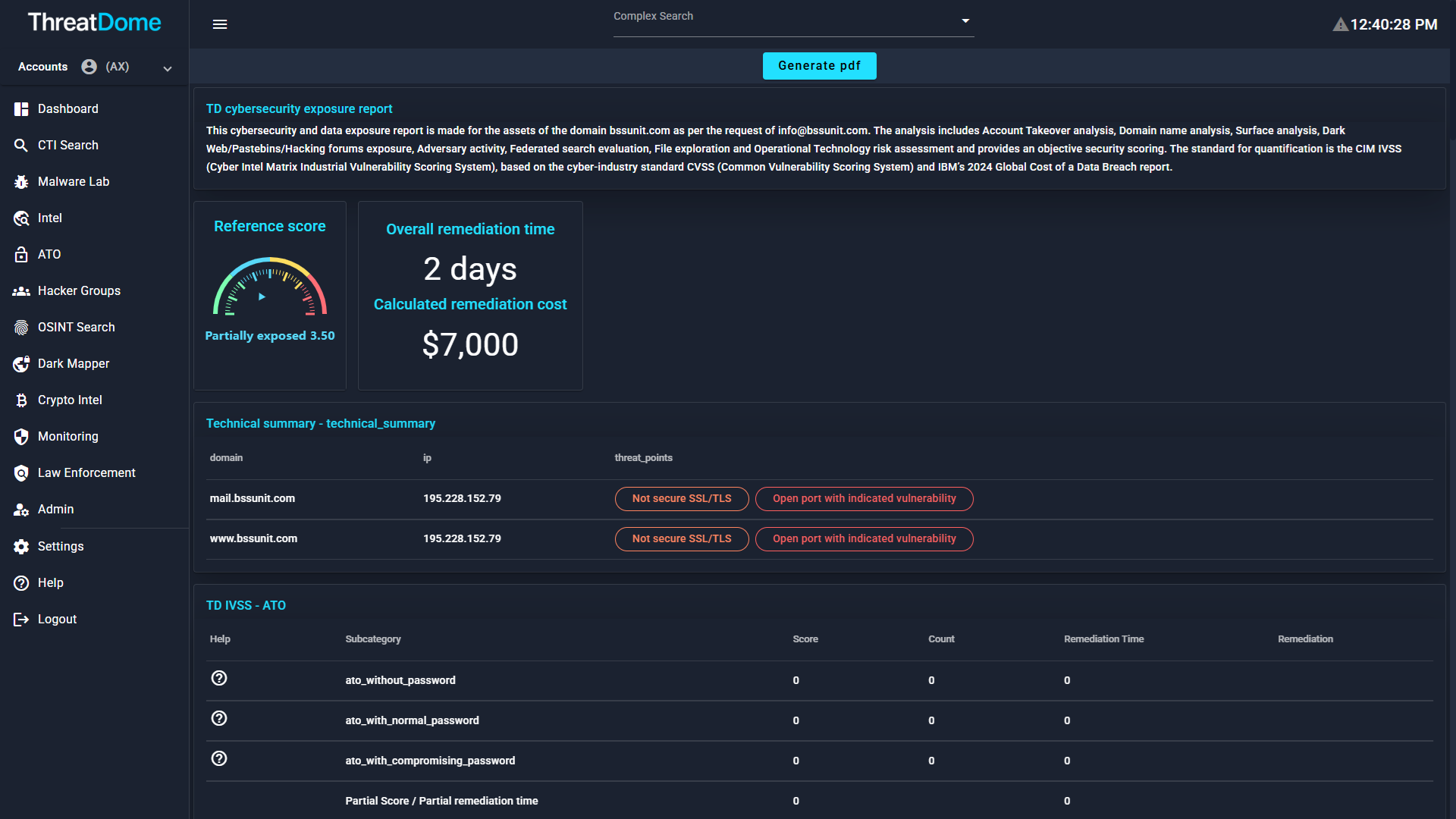
The Exposure Test service reflects a digital imprint of the company and its executives. A human expert analyst validates and details the automated intel findings.
The corporate Exposure Test is essentially a data exposure vulnerability scan.
The exposure assessment examines eight main aspects of essential infrastructure: Account Takeover (Breached Credentials) analysis, Domain name analysis, Surface analysis, Dark Web and Media exposure, Adversary activity, Federated search evaluation, File exploration, and Operational Technology risk assessment. The report gives an exposure score from 1 to 10 indicating the severity of each vulnerability and finally the extent of the overall risk, and offers some technical advice on mitigating the uncovered issues. The standard for quantification is the ThreatDome IVSS (ThreatDome Industrial Vulnerability Scoring System), based on the most widely accepted cyber-industry standard CVSS (Common Vulnerability Scoring System) and IBM’s annually published Global Cost of a Data Breach report.
The Exposure Test enables businesses to slam the door shut on hackers and get back to business. Here is how it works:
After the primary data collection, experienced analysts aggregate the data and place it in context. After completing the data evaluation, the system generates the report and it will be sent to you via e-mail within 2 business days of ordering.